Cybersecurity Teacher Carey Anderson
Cybersecurity Teacher Carey Anderson
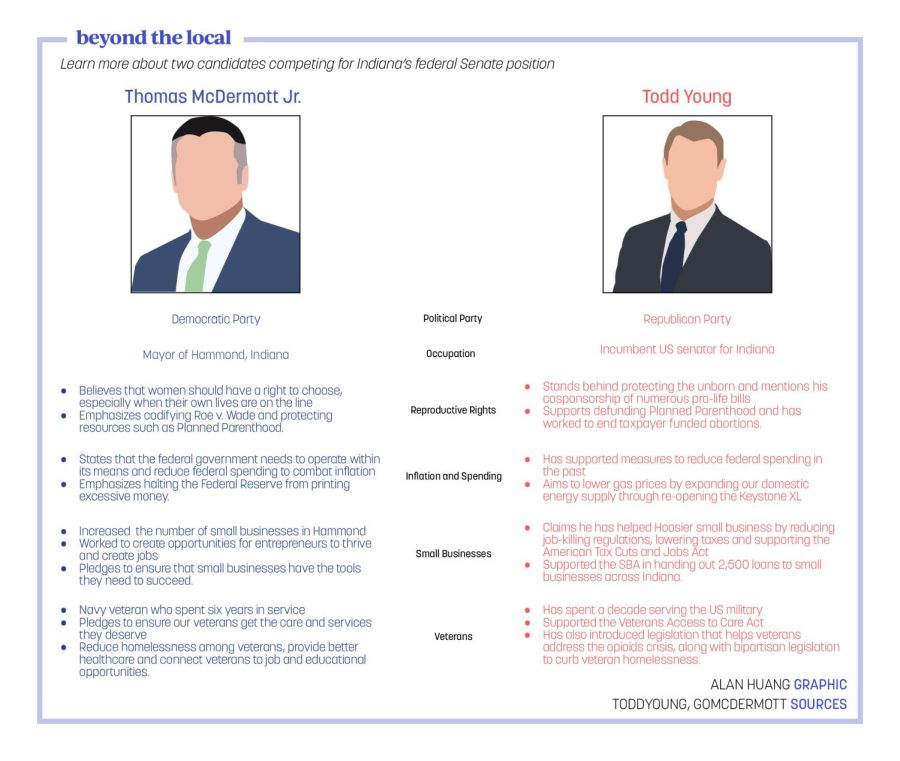
What classes do you teach here at CHS?
“I have personally taught Intro to Computer Science (and) Computer Science Principles, which is an AP course. I also teach Cybersecurity, which we (call) our CS3 Capstone class. And that is under Project Lead the Way (PLTW). And then I teach web design and I’ve also taught, in the past, Digital Applications and Responsibilities.”
What concepts are taught in the new cybersecurity class?
“It’s broken down into different units. We are right now focusing on what’s called ‘personal security’… So we really just want to teach students protection. But we also have network security. And then we also teach them the history of cybersecurity.”
How does this class compare to other classes that have been previously taught under computer science?
“Computer Science AP had a small unit and continues to have a small unit in (the area of cybersecurity)… what we’re doing (now) is just really opening up that one idea of cybersecurity because it also helps those people that already have programming experience, because they’re working on virtual machines, and so, basically, toward the end of the class my students will be working on three virtual machines and they’re trying to figure out where the vulnerability (is on those machines).”
Why is the Cybersecurity course being offered now?
“Really, toward universities, there is a huge growth right now in cybersecurity. We (also) realized there’s over 3000 (cybersecurity) jobs open in Indiana right now and they can’t fill them. So there’s a huge need in this area.”
Max Chang, Cyberpatriots co-president and senior
Can you first list the computer science clubs you’re involved in as well as classes you’ve taken in computer science?
“The main club that I am involved in is cyberpatriots. I am currently co-president with senior Jinhee Won. I have taken AP Computer Science Principles and am currently in PLTW Cybersecurity.”
How does PLTW Cybersecurity compare to other computer science courses this school offers?
“Cybersecurity offers a larger focus on cryptography and protection measures against malware or malicious actions. There is also a large emphasis on network security, which is different from the usual personal security. In other computer science courses there is a focus on programming but in cybersecurity there is little to no programming done. The majority of the work is enabling secure systems for personal and network devices. Cybersecurity is a lot more personal as well, since a lot of the information learned can be applied to our digital lives’

What concepts are used in Cyberpatriot club and how do those competitions work?
“Cyberpatriots is a national competition sponsored by the U.S. Air Force. For the majority of the competition, we are given virtual machines by cyberpatriots. These virtual machines are basically a computer inside a computer. So within your computer, you have another system. Within that system, there are security vulnerabilities that we have to solve, and for each one that we solve, we get a certain number of points. For the competition, we have Linux and Windows systems where we have to solve the vulnerabilities. The third part of the competition is Cisco or network vulnerabilities. For Cisco, you have to solve a packet tracer which is basically a network, and fixes the network so everything is connected. The concepts that we use are mainly in the area of cryptography and operational security.”

































![British royalty are American celebrities [opinion]](https://hilite.org/wp-content/uploads/2024/03/Screenshot-2024-03-24-1.44.57-PM.png)



















![Chelsea Meng on her instagram-run bracelet shop [Biz Buzz]](https://hilite.org/wp-content/uploads/2024/04/IMG_2446-1200x838.jpg)
![Review: Quiet on Set: The Dark Side of Kids TV is the long awaited exposé of pedophilia within the children’s entertainment industry [MUSE]](https://hilite.org/wp-content/uploads/2024/04/unnamed.jpg)
![Review: “The Iron Claw” cannot get enough praise [MUSE]](https://hilite.org/wp-content/uploads/2024/04/unnamed.png)
![Review: “The Bear” sets an unbelievably high bar for future comedy shows [MUSE]](https://hilite.org/wp-content/uploads/2024/03/unnamed.png)
![Review: “Mysterious Lotus Casebook” is an amazing historical Chinese drama [MUSE]](https://hilite.org/wp-content/uploads/2024/03/0.webp)
![Review in Print: Maripaz Villar brings a delightfully unique style to the world of WEBTOON [MUSE]](https://hilite.org/wp-content/uploads/2023/12/maripazcover-1200x960.jpg)
![Review: “The Sword of Kaigen” is a masterpiece [MUSE]](https://hilite.org/wp-content/uploads/2023/11/Screenshot-2023-11-26-201051.png)
![Review: Gateron Oil Kings, great linear switches, okay price [MUSE]](https://hilite.org/wp-content/uploads/2023/11/Screenshot-2023-11-26-200553.png)
![Review: “A Haunting in Venice” is a significant improvement from other Agatha Christie adaptations [MUSE]](https://hilite.org/wp-content/uploads/2023/11/e7ee2938a6d422669771bce6d8088521.jpg)
![Review: A Thanksgiving story from elementary school, still just as interesting [MUSE]](https://hilite.org/wp-content/uploads/2023/11/Screenshot-2023-11-26-195514-987x1200.png)
![Review: When I Fly Towards You, cute, uplifting youth drama [MUSE]](https://hilite.org/wp-content/uploads/2023/09/When-I-Fly-Towards-You-Chinese-drama.png)
![Postcards from Muse: Hawaii Travel Diary [MUSE]](https://hilite.org/wp-content/uploads/2023/09/My-project-1-1200x1200.jpg)
![Review: Ladybug & Cat Noir: The Movie, departure from original show [MUSE]](https://hilite.org/wp-content/uploads/2023/09/Ladybug__Cat_Noir_-_The_Movie_poster.jpg)
![Review in Print: Hidden Love is the cute, uplifting drama everyone needs [MUSE]](https://hilite.org/wp-content/uploads/2023/09/hiddenlovecover-e1693597208225-1030x1200.png)
![Review in Print: Heartstopper is the heartwarming queer romance we all need [MUSE]](https://hilite.org/wp-content/uploads/2023/08/museheartstoppercover-1200x654.png)















![Review: Ladybug & Cat Noir: The Movie, departure from original show [MUSE]](https://hilite.org/wp-content/uploads/2023/09/Ladybug__Cat_Noir_-_The_Movie_poster-221x300.jpg)

![Review: Next in Fashion season two survives changes, becomes a valuable pop culture artifact [MUSE]](https://hilite.org/wp-content/uploads/2023/03/Screen-Shot-2023-03-09-at-11.05.05-AM-300x214.png)
![Review: Is The Stormlight Archive worth it? [MUSE]](https://hilite.org/wp-content/uploads/2023/10/unnamed-1-184x300.png)