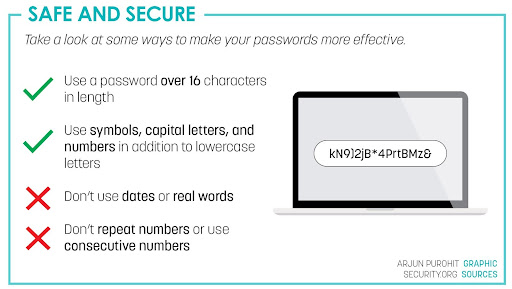
How do you define a strong password, and why is it important in today’s society?
Passwords protect a lot of super important information, lots of information that’s confidential. For example, bank accounts, confidential company specific secrets, (and) user accounts, especially when we’re talking about user accounts with privileges to do things. For example, administrational accounts are those (that) have to be kept really well protected and (can be attacked using) two different techniques. The first is just brute force password cracking. That’s where you try every single iteration of a potential password. That’s less commonly used than (the other technique), social engineering, which is (when) the attacker tries to get the victim to give them their password through (phishing) emails impersonating (the IT department). (They will send emails saying), ‘Hey, we need your password because we need to reset it.’ Well, if you believe it, you give them a password. You’ve just done all the work for (the hacker) because now they don’t need to actually crack it or use anything else.
What are some common problems people encounter when creating passwords, and how can they be avoided?
A lot of people have this misconception about passwords that they have to be super complicated. There’s always this trade-off with passwords between convenience and security. The more convenient a password is for you to remember, the more simple it is and the (easier) it is to crack. The more secure it is, the harder it’s going to be for you to remember. So it’s really convenient for people to remember that (there’s) a huge trade off that a lot of people face. There are a couple of ways that you can address that. Number one is to create a passphrase. That’s a string of seemingly random words. It’s actually really difficult for hackers to hack and break passphrases because of complexity requirements and the algorithms. Another alternative that you could use is a password manager. There are lots of great ones available online.
Can you explain the concept of passphrase and its advantages over traditional passwords?
A passphrase is three or more words that are connected by some letters and some symbols in between. There’s a really popular expression from a popular comic out there about how if you basically take three random words, (for example), grade, course and green, and then combine them together and then intersperse numbers or symbols in between, it would actually take much longer to crack than a typical randomized password and that’s because (passphrases) combine different words together. There’s a lot more possible combinations because it’s easy for you to remember but it also adds a lot of length and that adds a lot of complexity (to passwords) that’s difficult to crack.
What role do password managers play in creating and managing strong passwords? Are they recommended?
Password managers are a great way to manage your passwords. However, you have to be really careful with the ones that you pick. For example, (if they get) breached, then that’s all of your passwords that are gone. There’s the popular ones, like 1Password, (where) you only need to remember one password. However, there are other authentication methods that I honestly think are more secure, for example two-factor authentication or if you have certain security codes. Other authentication apps like (Duo Security) are honestly better and more effective than password managers.
With the rise of biometric authentication, do traditional passwords still hold relevance? If so, why?
I think, number one, (biometric authentication) has two different issues. The first one is Touch ID (which) can be easily hacked. If someone just gets a fingerprint they can use it in a lot of different ways, and that could be true. I think there’s also a lot of risks associated with providing your biometric data to any centralized source. It’s pretty private information, and I think it has a lot of potential to be misused.
How frequently should individuals change their passwords?
Good practice is maybe once every month or so. I can personally say that I have never once changed my passwords unless I forget them.
What are the key elements of a strong multi-factor authentication system, and why is it important to implement?
You want to use a secure method, so that would typically be through text messages or a phone call; however, these methods are easily spoofed, so I would recommend using third-party authentication apps like Duo Secure since they are more secure and reliable.
How do you suggest organizations educate their employees about the importance of strong passwords and security best practices?
There are websites online where you type in your password and it tells you how secure your passwords are. Those resources are really beneficial because you can see right away how strong your password is and the recommendations of what you should change. There are incredible resources out on the internet on how to create strong passwords, even ones that utilize games, and the gamification aspect encourages people to create stronger passwords.
Looking ahead, what advancements or technologies do you anticipate will shape the future of password security?
Especially with quantum computing, people are saying passwords are going to get hacked in a lot more easy ways. For example, GitHub has already implemented a new security system where it’s (an) embedded key matching system that a lot of people have already implemented. There’s a lot of innovations that we’re seeing. Also, recently, there (was) a breach in a very famous password hashing algorithm where people found out that someone had pointed a backdoor in open source code that was used to attack this verification method of a very popular third-party key. We’re seeing a lot of threats being used, but I would also say that we’re also seeing technology progress. Just because quantum computing can (crack and find) the right passwords doesn’t mean that we can’t also use quantum computing to develop additional security measures and safeguards to protect our security. Also, we’re seeing more and more authentication measures that aren’t just password-based. Two-factor verification (is) becoming pretty much common practice everywhere, and we’re also seeing innovations in other areas. It’s like a cat-and-mouse game. One side progresses, and the other side progresses as well.





























![Family vlogger controversy, need for content reform [opinion]](https://hilite.org/wp-content/uploads/2024/05/Screenshot-2024-05-14-11.33.37-AM-1200x465.png)



























![Review: Taylor Swift’s new album The Tortured Poets Department is not her best work but is still a brilliant album [MUSE]](https://hilite.org/wp-content/uploads/2024/05/The-Anthology_Cover-1200x675.webp)
![Review: Challengers does it all [MUSE]](https://hilite.org/wp-content/uploads/2024/05/challengers-poster-1200x600.png)
![Review: A House of Flame and Shadow by Sarah J. Maas was a disappointing read [MUSE]](https://hilite.org/wp-content/uploads/2024/05/house-of-flame-and-shadow-feature.png)
![Review: Conan Gray’s new album, “Found Heaven”, is a refreshing twist on modern music [MUSE]](https://hilite.org/wp-content/uploads/2024/05/Screenshot-2023-10-31-at-16.01.05.webp)
![Review: “Bodies, Bodies, Bodies” is the quintessential Gen-Z movie [MUSE]](https://hilite.org/wp-content/uploads/2024/05/Screenshot-2024-05-15-140618.png)
![Review in Print: Maripaz Villar brings a delightfully unique style to the world of WEBTOON [MUSE]](https://hilite.org/wp-content/uploads/2023/12/maripazcover-1200x960.jpg)
![Review: “The Sword of Kaigen” is a masterpiece [MUSE]](https://hilite.org/wp-content/uploads/2023/11/Screenshot-2023-11-26-201051.png)
![Review: Gateron Oil Kings, great linear switches, okay price [MUSE]](https://hilite.org/wp-content/uploads/2023/11/Screenshot-2023-11-26-200553.png)
![Review: “A Haunting in Venice” is a significant improvement from other Agatha Christie adaptations [MUSE]](https://hilite.org/wp-content/uploads/2023/11/e7ee2938a6d422669771bce6d8088521.jpg)
![Review: A Thanksgiving story from elementary school, still just as interesting [MUSE]](https://hilite.org/wp-content/uploads/2023/11/Screenshot-2023-11-26-195514-987x1200.png)
![Review: When I Fly Towards You, cute, uplifting youth drama [MUSE]](https://hilite.org/wp-content/uploads/2023/09/When-I-Fly-Towards-You-Chinese-drama.png)
![Postcards from Muse: Hawaii Travel Diary [MUSE]](https://hilite.org/wp-content/uploads/2023/09/My-project-1-1200x1200.jpg)
![Review: Ladybug & Cat Noir: The Movie, departure from original show [MUSE]](https://hilite.org/wp-content/uploads/2023/09/Ladybug__Cat_Noir_-_The_Movie_poster.jpg)
![Review in Print: Hidden Love is the cute, uplifting drama everyone needs [MUSE]](https://hilite.org/wp-content/uploads/2023/09/hiddenlovecover-e1693597208225-1030x1200.png)
![Review in Print: Heartstopper is the heartwarming queer romance we all need [MUSE]](https://hilite.org/wp-content/uploads/2023/08/museheartstoppercover-1200x654.png)











![Review: “Ginny & Georgia” is a dramatic and poorly made emotional rollercoaster–and I loved it anyway [MUSE]](https://hilite.org/wp-content/uploads/2024/03/ginny-and-georgia-season2-main-be37bbb9487a41e88b3f66c3baacd5c3-300x177.jpg)
![Review: Witch Hat Atelier is a masterpiece in art and world-building, but the story has only begun [MUSE]](https://hilite.org/wp-content/uploads/2024/01/unnamed-211x300.png)
![Review: “Mysterious Lotus Casebook” is an amazing historical Chinese drama [MUSE]](https://hilite.org/wp-content/uploads/2024/03/0-300x170.webp)
![Review: “A Little Life” by Hanya Yanagihara is the epitome of a heartwrenching masterpiece [MUSE]](https://hilite.org/wp-content/uploads/2024/01/unnamed-5-300x200.png)


